Secure360
Security Awareness Training
Why Security Awareness Training
Because 95% of data breaches are caused by human error. Ransomware, email phishing, phone scams and many more involve untrained staff doing the wrong thing. No antivirus or firewall can protect you against your staff’s errors.


Why My Staff Need Security Training? Because They Are …
- getting emails from Nigerian spammers and ransomware emails and are clicking on it
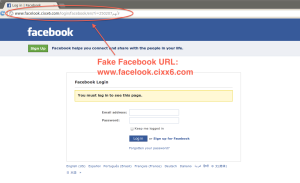
- getting fake emails from banks and logging to those websites
- using public wireless to log into social network, banks, etc and have their password stolen.
- using the word: password or 12345 as their password
- leaving their laptops in the car and have it stolen
- sending personally identifiable information (PII) via emails
- using personally owned phones and laptops without properly securing them.
How
- Regularly, we train, test, create reports and certify users based on training and test results.
- Ongoing training keeps security top of mind
- Training reports for all users or a specific group (who started, completed, started but never finished)
- Details on enrollment %, course started %, incomplete %, completed course, acknowledged security policy

Training Topics
- Interactive, engaging modules, videos, games, posters and newsletters. Automated training campaigns with scheduled reminder emails.
- Internal and External Threats
- Compliance based training (HIPAA, PCI)
- Phishing scams (to get company or your personal data)
- In-depth review - Video on spotting phishing scams - Interactive quiz - Can you spot a phish?
- Phone scams (to get your SSN, credit card number, PII)
- Passwords
- Wi-Fi dangers
- Physical protection – devices
- BYOD – mobile devices- dangers
- Clean desk policy
- Training content is continually updated
Testing
Empower your employees to better manage the urgent IT security problems of social engineering, spear-phishing and ransomware attacks.
Simulated Phishing Attack Platform and Security Test
Did you know that 91% of successful data breaches started with a spear-phishing attack? Find out what percentage of your employees are Phishing prone with our phishing security test
Over the last few years, thousands of organizations in the U.S have started to phish their own users. IT pros have realized that doing this is urgently needed as an additional security layer. Today, phishing your own users is just as important as having antivirus and a firewall.
- Fake Phishing Emails Test Employee Awareness
- Ability to Track and Report Employee Actions
- Custom Campaign Configuration Options based on your industry and requirements
- Successful Attacks redirected to Landing Page for further training
- Social Engineering Indicators™ patent-pending technology, turns every simulated phishing email into a tool you can use to dynamically train employees by instantly showing them the hidden red flags they missed within that email
- Top 10 Criminal Phishing Emails of the week - defanged and ready to send to employees
- Automatic "Scam Of The Week" Campaign - sent to all employees

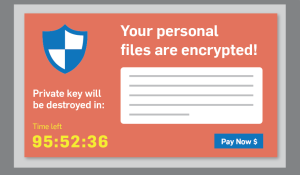
Ransomware Simulator & Testing
How vulnerable is your network against ransomware infections?
Bad guys are constantly coming out with new versions of ransomware strains to evade detection. Is your network effective in blocking ransomware when employees fall for social engineering attacks?
Secure360’s Ransomware Simulator gives you a quick look at the effectiveness of your existing network protection. The simulator will simulate multiple ransomware infection scenarios on a regular basis and show you if a workstation is vulnerable to infection.
USB Security Test
Did you know? On average 45% of your users will plug in USBs...
Find out now what your user’s reactions are to unknown USBs, with KnowBe4's new Free USB Security Test.
USB Drive security test allows you to test your user’s reactions to unknown USBs they find


Vishing
Vishing is the phone's version of email phishing and uses automated voice messages to steal confidential information. The term is a combination of "voice" and "phishing."
Test your end-users with simulated interactive voice response (IVR) attacks over the phone
Social Engineering
Artificial Intelligence Driven Method which combines phishing, vishing, smishing in to a new social engineering attack vector coined as "aishing™".


Annual Security Risk Assessment
- Comprehensive onsite and offsite Risk Assessment and Report
- Additional Security Recommendations
- Threats Analysis / Risk Determination
Reporting
- "Phishing Reply Tracking" allows you to track if a user replies to a simulated phishing email and can capture the information sent in the reply
- Filter campaigns on recipient, delivered, opened, clicked, attachment, data entered, bounced,
- Individual user "report cards" with their “open and click” history
- Top 50 clickers report
- Personal time-line overview for every individual user
- Phishing Reply Tracking reports with who answered and what they said


Security Policies and Procedures
- Electronic Acknowledgment of Policies
- Administrator Report of Policy Acknowledgment













